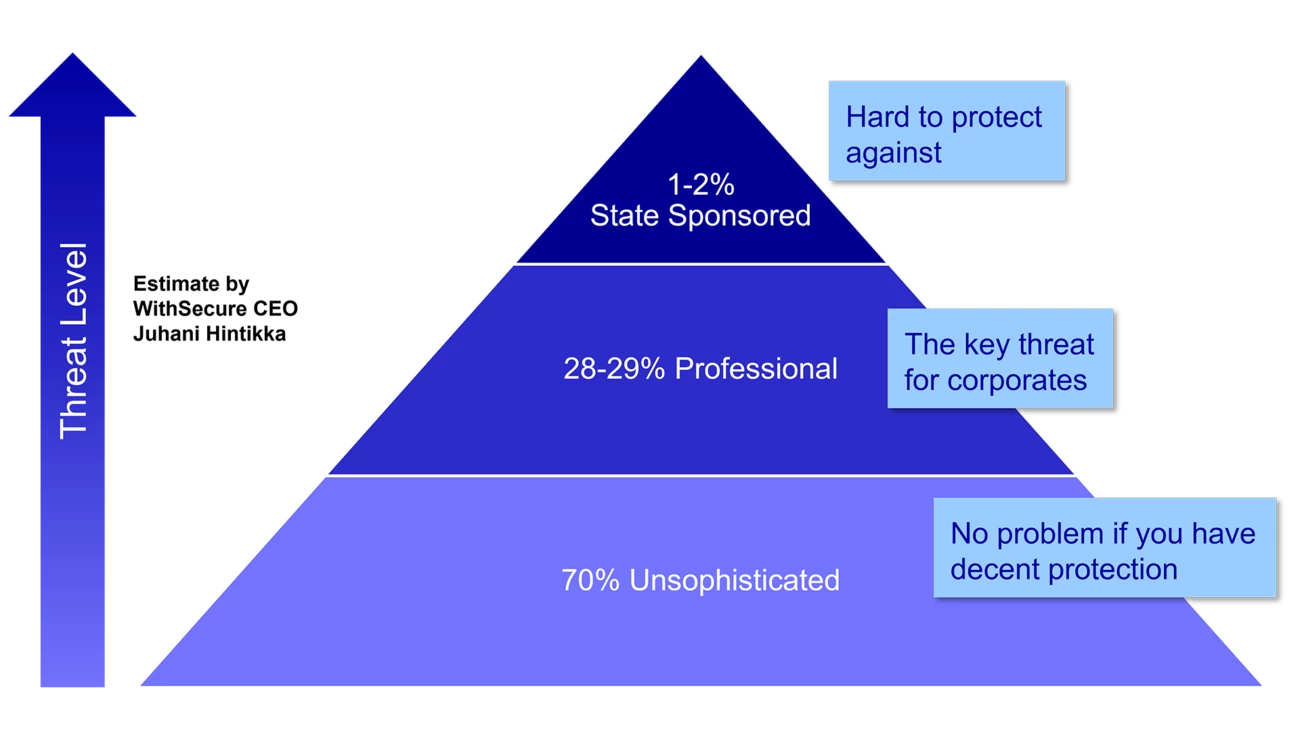
The key to cybersecurity is basic IT hygiene, which can be strengthened through staff training. In today's complex and evolving threat environment, WithSecure CEO Juhani Hintikka (JH) advises companies to team up with a partner to make the best use of their chosen tools and solutions and meet their cybersecurity needs.
In this interview with Nordea On Your Mind author Johan Trocmé (JT), the Finnish CEO also shares his thoughts on key cybercrime drivers, threats and basic defence.
JT: Cybercrime has grown, and unfortunately seems to continue to grow, very rapidly. What are the key drivers behind this?
JH: For starters, virtually all businesses have become much more digital today, and this has evolved very rapidly from ten years ago. We have all become very dependent on information technologies, and this applies to both new and older traditional industries. The world's existing data volumes have grown exponentially, and that data is vulnerable to crime. This gives you some context for the growth in cybercrime.
Another driver is that payment mechanisms have evolved, and the advent and spread of cryptocurrencies have facilitated the use of ransomware – a variety of cybercrime that has soared in recent years. The availability of an untraceable money transfer mechanism with a currency unit and a value that criminals can monitor and realise has contributed to making ransomware activity more 'industrial'. Indeed, we have seen the emergence of the first 'criminal unicorns'. These are criminal groups that are essentially run as enterprises, which unfortunately implies that they have the means and the ability to be the best at what they do. For such criminals, their cybercrimes are technoeconomic business cases.
There are other forms of online crime, too. After WikiLeaks rose to fame in 2006, a leaks culture became established. Money is a huge driver of cybercrime, but there is also a willingness to protest or influence online. Technology has made it possible to do so anonymously. This is not only a negative – I think it forces companies to be ethical and helps ensure that they have whistleblower channels and processes in place.
One worrying development is that we have started to see artificial intelligence (AI) used in cyberattacks. The challenge for defenders will be to create more automated response to AI-originated attacks. At WithSecure, we have invested in AI since many years, and built some familiarity with it. But the success and popularity of, for example, ChatGPT, has popularised the topic. And sadly, cybercrime will become another application for AI. It can be used to write malicious code. It can also help in devising ways to spread and mutate. In the execution of actual attacks, hackers can use AI to anticipate defenders' actions. With machine learning, attack algorithms can be trained on data for most common defensive responses.
Cyber criminals are becoming more professional. Like other corporations, they have customer service, a reputation and a brand. If you pay them after suffering a ransomware attack, they will typically release your data. If they don't, their criminal reputation will suffer, and their criminal brand will be tarnished.
JT: If you compare cybercrime today with the situation ten years ago, how would you say it has evolved?
JH: I would say there are two major types of cybercrime. There are the ransom Trojans. When ransomware is used, the attacker takes control of their target's data after a breach in the target's system. The data is then usually encrypted, but we have recently seen examples of the data being moved somewhere out of reach for the target. A ransom is demanded for the release of the data. These attacks are usually perpetrated by quite well-organised criminal groups, whose intent is to extort and make money. The consequences of ransomware attacks can be devastating, on the human, as well as the corporate operational and financial levels. This is illustrated well by the attack against the Finnish private psychotherapy service provider Vastaamo in 2020, in which confidential patient records were compromised. After a failed extortion attempt against the company, the attacker approached the patients whose records had been stolen directly, trying to extort them instead. It became the biggest criminal case in Finnish history, with some 30,000 victims. What really stood out was how the attacker cruelly and underhandedly targeted some of the most vulnerable targets imaginable. Many of us in the industry were stunned by the human suffering caused, and reminded of how the damage from cybercrime is not only about the money.
The second main type of cybercrime is the business email compromise (BEC) scam, in which attackers create authentic-looking emails with payment instructions. There have been several incidents reported, particularly by public companies required to disclose such information, about emails from CEOs with instructions to make a substantial payment to a specified account or recipient. Back when I was the CEO for a previous employer, before entering the cybersecurity industry, I had a personal experience with a BEC attack. Our head of external accounting received an email from me, the CEO, with instructions to pay a quite substantial sum of money. It all seemed legitimate, but she started thinking about the instruction and how it came about, so she walked into my office and asked if I had sent it. My reply was 'no', after which she rang the police. We were able to stop the payment, and did not suffer any financial damage on that occasion. But we could easily have faced financial repercussions.